How Long Should A Password Be
Think your password is secure enough?
You lot may want to recollect again. In 2014, well-nigh half of Americans had their personal info exposed by hackers – and that doesn't even count the many companies that experienced breaches.
And with more than and more businesses storing their information in the cloud and using SaaS solutions similar business organisation intelligence and 60 minutes software platforms, keeping your information safe becomes fifty-fifty more than of import.
Selecting an obscure and complex password and changing it frequently tin can spell the departure between keeping your data secure and having your personal information stolen. Nosotros've gathered insights and communication to empower yous to tighten up your online security – and proceed hackers out of your personal business organization.
To get started, we set out to discover just how speedily a seasoned cracker could "brute-force" diverse types of passwords (systematically check combinations until finding the right one) based on factors such every bit length and character types. We also created an interactive feature that lets you gauge how long it would take someone to cleft a password now compared with how long it took in the past. If you come upward with an thought for a potential password, our tester can tell yous just how secure it is. Just how many days, weeks, or years worth of security an actress letter or symbol make? How does countersign strength change over fourth dimension? The answers just might surprise you lot.
How strong is a typical countersign now – and how strong was information technology in the 1980s? Enter a word (non your current password) and drag the slider to select a year to observe out how long information technology would take for someone to crack the term if it were your password. Information technology could have anywhere from infinite time to a millennium to mere fractions of a millisecond.
You can turn the "word listing" part on or off as you test passwords. This tool works by cycling through a word list containing mutual words and passwords and and then evaluating other factors such as character types. If y'all enter a password not on the word list, the smashing time will not be affected. But if your password is on the discussion list, it greatly affects corking time.
Note: The interactive tool is for educational purposes just. Although it does not collect or store your passwords, you should avoid using your current countersign.
How long should your password exist?
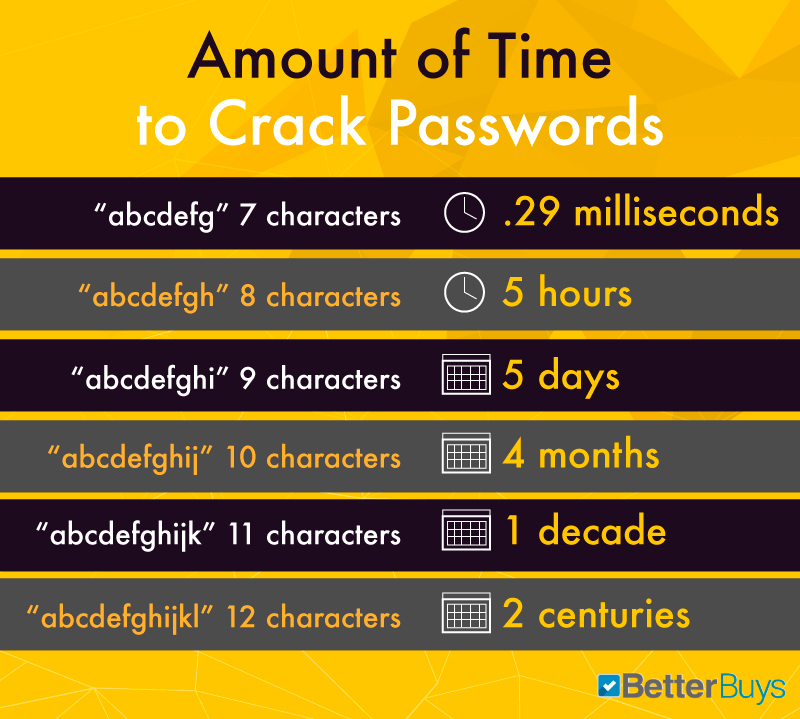
When it comes to passwords, one affair is certain: Size matters. Calculation a single character to a password boosts its security exponentially. In a so-chosen "dictionary attack," a countersign cracker will utilize a word list of common passwords to discern the correct i. The listing above shows the difference that calculation characters tin can make when it comes to security.
For example, if you lot take an extremely simple and common password that's seven characters long ("abcdefg"), a pro could crevice information technology in a fraction of a millisecond. Add but one more character ("abcdefgh") and that time increases to 5 hours. 9-character passwords take five days to break, 10-character words accept four months, and 11-graphic symbol passwords accept 10 years. Brand information technology up to 12 characters, and you're looking at 200 years' worth of security – not bad for one little letter.
blastoff and numberic characters
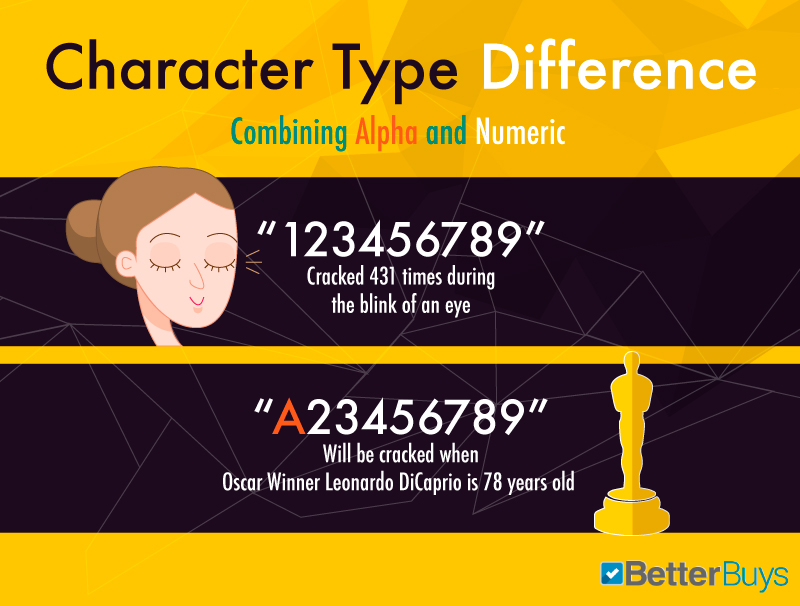
Combining numbers and letters rather than sticking with one type of character dramatically enhances password security. A string of 9 letters or numbers takes milliseconds to crack. Add together a single letter, and your countersign may go ambiguous enough to thwart password crackers for nearly four decades.
Even so, it's not equally unproblematic as swapping your "east" for a "3" or adding a number at the stop of a cord of letters. Countersign attacking methods actually take advantage of those common habits. Your best bet is to simply make your countersign less predictable and more complicated.
asci, lowercase, and numeric characters

Combining several types of characters is an extremely effective way to make your password more cryptic. A simple, common word tin can be cracked in fractions of a millisecond. Inject a mix of lowercase and capital letter letters, numbers, and symbols (remember @, %, and #), and your password tin be secure for more a decade.
password strength over fourth dimension
.jpg)
Not every security issue comes downwardly to password character types and length – time is also a major factor. Over the years, passwords weaken dramatically as technologies evolve and hackers become increasingly proficient. For example, a password that would accept over 3 years to crack in 2000 takes just over a yr to crack by 2004. Five years later, in 2009, the bully time drops to iv months. By 2016, the aforementioned password could be decoded in just over two months. This demonstrates the importance of changing passwords frequently.
what if you get hacked?
.jpg)
One morning, y'all open up your electronic mail, and everything has gone haywire: Friends are chatting y'all to say they've received spam from your address. Your login history looks odd. Y'all have a pile of bounce-back letters in your inbox and a bunch of foreign messages in your sent box. You've been hacked – so what should you exercise?
Start, recover your electronic mail account, and modify your password (employ our guidelines to codify a stiff one). Complete all the steps, such equally changing security questions and setting upwards phone notifications. Because email is filled with personal information, y'all should also notify your bank, PayPal, online stores, and any other accounts to discern whether a breach has occurred. Be sure to change other passwords likewise. Finally, notify your contacts in case emails sent from your account have compromised their information too. While not getting hacked at all is the all-time-case scenario, promptly taking these steps can make the best of a bad situation.
Protect yourself
As fourth dimension goes on, information technology only becomes more than probable that your password will exist hacked – putting your most personal information at risk. By taking a few steps to enhance your password, you lot can exponentially minimize the run a risk of a breach. When it comes to passwords, size trumps all else – so choose i that'southward at least xvi characters. And be certain to choose a mix of grapheme types (numbers, capital letter and lowercase letters, and symbols) to further raise its security.
What else tin can you lot do? Steer articulate of words found in the dictionary, pronouns, usernames, and other predefined terms, besides as commonly used passwords – the height two in 2015 were "123456" and "countersign" (yes, you read that correct). As well, never apply the same password in different places (that forgotten business relationship at a site you never use could lead to a bank business relationship alienation). Consider using a password generator in order to get a complex password with no discernible blueprint to assistance thwart password crackers. Finally, if memorizing long strings of characters proves too taxing, consider adopting a countersign manager that stores all your passwords. No password is perfect, but taking these steps tin can get a long way toward security and peace of mind.
Methodology
Using processor data nerveless from Intel and John the Ripper benchmarks, we calculated keys per second (number of countersign keys attempted per 2d in a brute-force attack) of typical personal computers from 1982 to today.
The results from our interactive feature may differ from those of other online password-testing tools due to factors such as different equations, processors, and discussion lists.
Our data are based on the following equations:
Number of possible character combinations:
(Countersign Blazon)^(Password Length)
Password Type is the number of possible characters.
Effective Cores:
one/((1-Efficiency Constant)+(Efficiency Constant/Processor Cores)) The Efficiency Constant we used is 0.99, and nosotros assume that 99% of the processor'south operations tin can be defended to the password fissure.
Processor GFLOPS:
Processor Frequency * Effective Cores
Keys Per 2nd:
GFLOPS/Encryption Constant (gathered and calculated from John the Ripper benchmarks).
Time in seconds:
Seconds = Combinations/KeysPerSecond
Sources
- http://ark.intel.com/#@Processors
- http://openwall.info/wiki/john/benchmarks#John-the-Ripper-benchmarks
- https://www.d.umn.edu/~gshute/arch/functioning-equation.xhtml#example
- https://www.pugetsystems.com/labs/articles/Estimating-CPU-Operation-using-Amdahls-Law-619/
- http://csrc.nist.gov/archive/pki-twg/y2003/presentations/twg-03-05.pdf
- http://money.cnn.com/2014/05/28/technology/security/hack-data-breach/
- http://gizmodo.com/the-25-most-pop-passwords-of-2015-were-all-such-id-1753591514
- http://world wide web.geekwire.com/2016/v-information-security-resolutions-y'all-cant-afford-to-ignore/
- http://www.ucl.ac.uk/media/library/blinking
- http://www.nps.gov/moru/faqs.htm
- http://lightning.nsstc.nasa.gov/primer/primer2.html
Fair Use
Feel gratuitous to share the images and interactive institute on this page freely. When doing so, please attribute the authors past providing a link back to this page and Better Buys, then your readers can acquire more than about this project and the related inquiry.
Source: https://www.betterbuys.com/estimating-password-cracking-times/
Posted by: millerprioner1938.blogspot.com


0 Response to "How Long Should A Password Be"
Post a Comment